We are growing our paid subscribers. It increases our responsibility towards user security and privacy.
Our commitment to user security and privacy is unwavering.
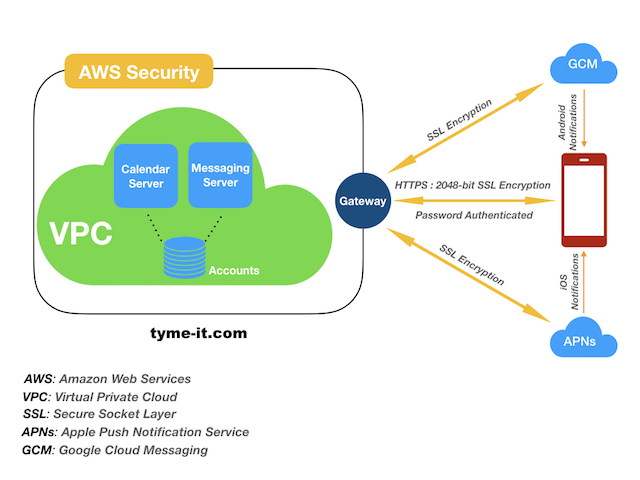
TymeIt uses AWS for its infrastructure. With AWS, the biggest security breach is unauthorized access to root/admin privileges and passwords. In no time, the entire platform can be shut down and data wiped out resulting in Denial-of-Service (DoS) attack.
To make sure our AWS security is not breached, we employ these practices.
Download TymeIt now to plan and schedule meetings.
Aug 13, 2018